Which of the following threat intelligence is used by a SIEM for supplying the analysts with context and "situational awareness" by using threat actor TTPs, malwarecampaigns, tools used by threat actors.
1.Strategic threat intelligence
2.Tactical threat intelligence
3.Operational threat intelligence
4.Technical threat intelligence
A major financial institution has strict policies preventing unauthorized data transfers. As a SOC analyst, during routine log analysis you detect an anomaly: an employee workstation initiates large file transfers outside business hours, involving highly sensitive customer financial records. You discover remote access from an unfamiliar IP address and an unauthorized USB device connection on the workstation. Given the likelihood of data exfiltration, what should be your first step in responding?
Which of the following stage executed after identifying the required event sources?
A large financial institution has identified a sophisticated phishing campaign targeting employees, resulting in unauthorized access to sensitive customer data. The organization already uses a SIEM for log aggregation and alerting, alongside an EDR solution for endpoint visibility. Additionally, they have access to XDR for broader threat detection and XSOAR for security orchestration and automation. As a SOC analyst, you’ve been asked to recommend an integration strategy to improve real-time threat correlation, streamline incident response workflows, and maximize the use of existing tools. Which integration would meet these goals?
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.
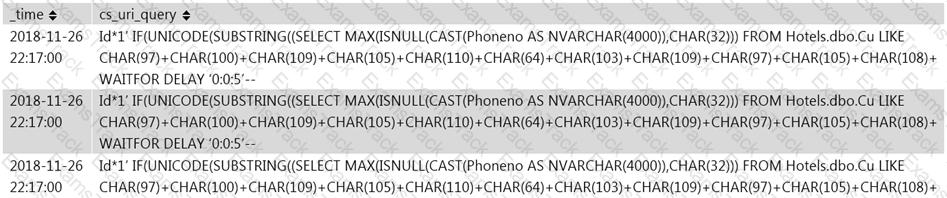
What does this event log indicate?
An organization is implementing and deploying the SIEM with following capabilities.
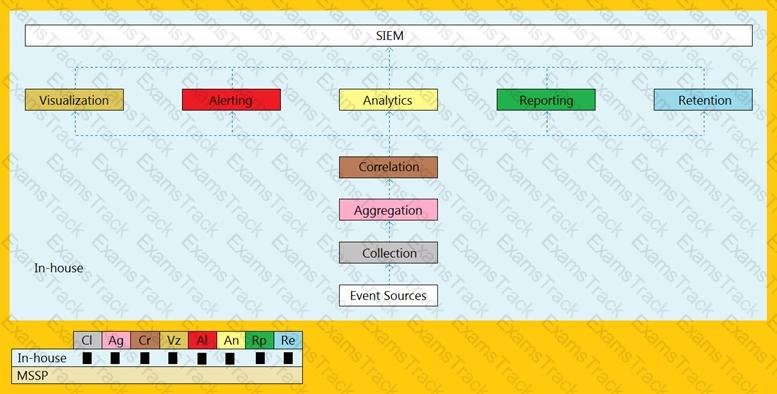
What kind of SIEM deployment architecture the organization is planning to implement?
Which of the log storage method arranges event logs in the form of a circularbuffer?
Secuzin Corp. is a large enterprise performing millions of financial transactions daily, making it critical to analyze security logs efficiently, detect suspicious activities, and respond to incidents in real time. Its SOC is responsible for managing security logs from various network devices, including firewalls, intrusion detection systems (IDS), authentication servers, and cloud services. To fulfill compliance and regulatory requirements that mandate long-term archival of logs, you need to provide a log storage solution that is scalable to handle increasing log volumes, provides encryption for data security, and is seamlessly accessible. Which storage solution should you choose to meet these long-term log storage requirements?
A multinational financial institution notices unusual network activity during a routine security audit. The SOC detects multiple failed login attempts, followed by a successful access attempt using an administrator's credentials from an unrecognized IP address. Shortly after, sensitive customer records are accessed without authorization. The company suspects a breach and calls in the forensic investigation team. During evidence collection, the forensic team creates a detailed record that tracks every individual who handled the evidence, its storage location, and timestamps of transfers. What is this process called?
What is the process of monitoring and capturing all data packets passing through a given network using different tools?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
ECCouncil Free Exams |
|---|

|