An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information system-description and platform-type to profile Cisco IP phones and allow access. Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
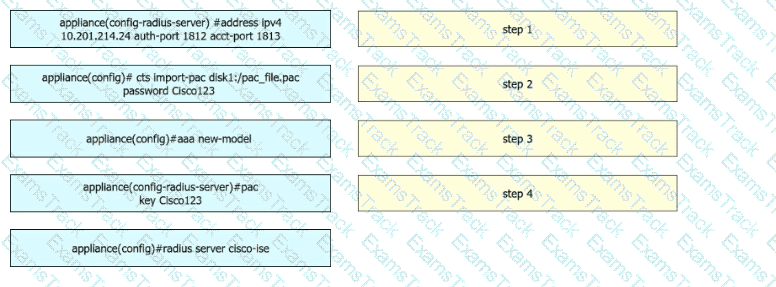
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco IISE. Drag and drop the commands from the left into sequence on the right. Not all options are used.
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
An administrator adds a new network device to the Cisco ISE configuration to authenticate endpoints to the network. The RADIUS test fails after the administrator configures all of the settings in Cisco ISE and adds the proper configurations to the switch. What is the issue"?
What are two requirements of generating a single signing in Cisco ISE by using a certificate provisioning portal, without generating a certificate request? (Choose two )
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
An engineer is starting to implement a wired 802.1X project throughout the campus. The task is to ensure that the authentication procedure is disabled on the ports but still allows all endpoints to connect to the network. Which port-control option must the engineer configure?
Which Cisco ISE solution ensures endpoints have the latest version of antivirus updates installed before being allowed access to the corporate network?
A network engineer is configuring guest access and notices that when a guest user registers a second device for access, the first device loses access What must be done to ensure that both devices for a particular user are able to access the guest network simultaneously?
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|