A network engineer has been tasked with enabling a switch to support standard web authentication for Cisco ISE. This must include the ability to provision for URL redirection on authentication Which two commands must be entered to meet this requirement? (Choose two)
Which two Cisco ISE deployment models require two nodes configured with dedicated PAN and MnT personas? (Choose two.)
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
An engineer is configuring a virtual Cisco ISE deployment and needs each persona to be on a different node. Which persona should be configured with the largest amount of storage in this environment?
An organization is adding nodes to their Cisco ISE deployment and has two nodes designated as primary and secondary PAN and MnT nodes. The organization also has four PSNs An administrator is adding two more PSNs to this deployment but is having problems adding one of them What is the problem?
An organization wants to split their Cisco ISE deployment to separate the device administration functionalities from the mam deployment. For this to work, the administrator must deregister any nodes that will become a part of the new deployment, but the button for this option is grayed out Which configuration is causing this behavior?
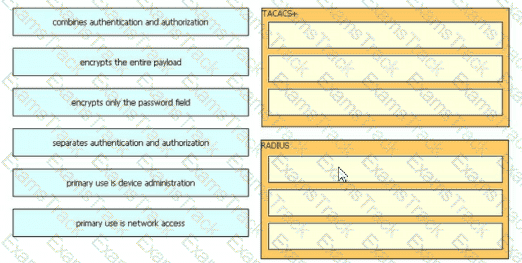
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
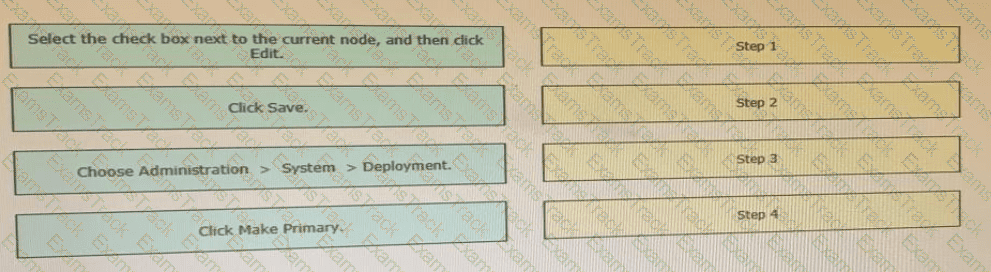
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the night.
What service can be enabled on the Cisco ISE node to identity the types of devices connecting to a network?
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|