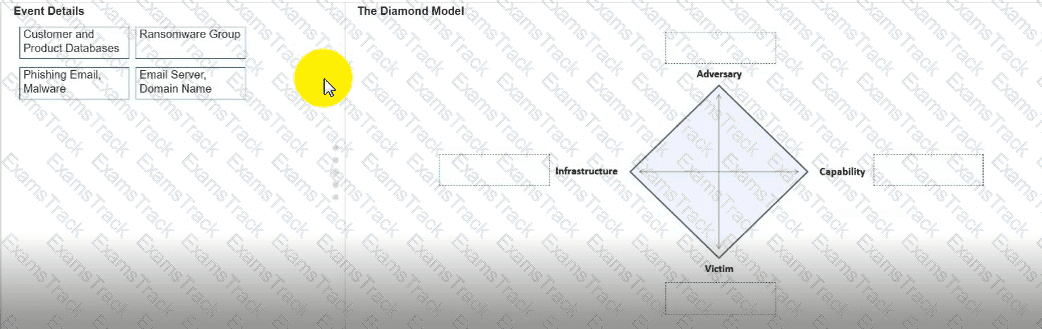
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
You are going to perform a penetration test on a company LAN. As part of your preparation, you access the company’s websites, view webpage source code, and run internet searches to uncover domain information. You also use social media to gather details about the company and its employees.
Which type of reconnaissance activities are you performing?
Move each NIST Incident Response Lifecycle phase from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.

Which wireless security protocol provides the strongest protection for a home or small business network?
Which macOS security feature encrypts the entire macOS volume?
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|