You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?
Which security assessment of IT systems verifies that PII data is available, accurate, confidential, and accessible only by authorized users?
You are planning to work from home. Your company requires that you connect to the company network through a VPN.
Which three critical functions do VPNs provide to remote workers?(Choose 3.)
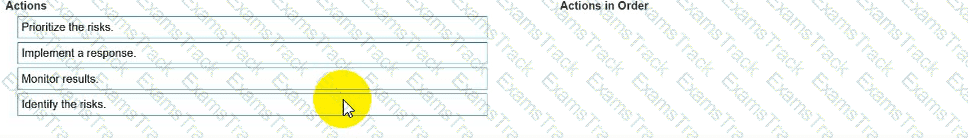
You need to manage security risks at your company. In which order should you complete the actions?
Move all the actions to the answer area and place them in the correct order.
How do threat actors launch ransomware attacks on organizations?
Which encryption type is commonly used to secure WiFi networks?
Which two basic metrics should be taken into consideration when assigning a severity to a vulnerability during an assessment?(Choose 2.)
Which security measure can prevent unauthorized devices from automatically connecting to a corporate network through unused switch ports?
A restaurant installs a second wireless router that only employees can use.
Which statement describes how to securely configure the new router?
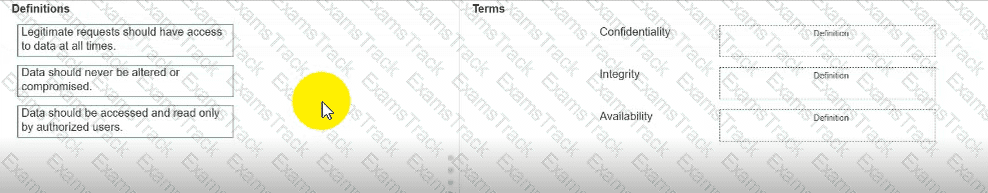
Move each definition from the list on the left to the correct CIA Triad term on the right.
Note: You will receive partial credit for each correct answer.
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|