What is the workflow to chain a Document Transformation system to a Connector integration for the purpose of transforming the output?
Refer to the following XML to answer the question below.

Within the template which matches on wd:Report_Entry, you would like to conditionally process the wd:Education_Group elements by using an
A calculated field used as a field override in a Connector is not appearing in the output. Assuming the field has a value, what could cause this to occur?
You have a population of workers who have put multiple names in their Legal Name - First Name Workday delivered field. Your third-party vendor only accepts one-word first names. For workers that have included a middle name, the first and middle names are separated by a single space. You have been asked to implement the following logic:
* Extract the value before the single space from the Legal Name - First Name Workday delivered field.
* Count the number of characters in the extracted value.
* Identify if the number of characters is greater than.
* If the count of characters is greater than 0, use the extracted value. Otherwise, use the Legal Name - First Name Workday delivered field.
What functions are needed to achieve the end goal?
How do you initially upload the XSLT file to a Document Transformation integration system?
You are creating an outbound connector using the Core Connector: Organization Outbound template. The vendor has provided the following requirements for how the data should appear in the output file.
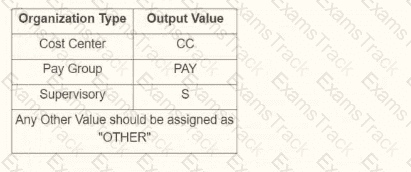
The vendor would also like to change the default document retention policy of 30 days to 7 days. What tasks do you need to use to configure this in your connector?
Refer to the scenario. You are implementing a Core Connector: Worker integration to send employee data to a third-party active employee directory. The external vendor requires the following:
The Employee's Active Directory User Principal Name.
A mapping from Worker Type values to external worker type codes.
A specific filename format that includes a timestamp and sequence number.
You also need to ensure the document transformation occurs before the file is delivered to the endpoint. You must include an Employee’s Active Directory User Principal Name (generated by a Calculated Field).
How do you ensure this field is pulled into the output?
You need the integration file to generate the date format in the form of "31/07/2025" format
• The first segment is day of the month represented by two characters.
• The second segment is month of the year represented by two characters.
• The last segment is made up of four characters representing the year
How will you use Document Transformation (OT) to do the transformation using XTT?
What is the purpose of declaring and defining the namespace in an XSLT stylesheet?
What is the relationship between the Integration System User (ISU), Integration System Security Group (ISSG), and domain security policies?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Workday Free Exams |
|---|

|