Which two types of Kubernetes member objects can be used when creating groups to collect and manage objects for service-level networking/security policies (for example, in a service mesh or Kubernetes-aware policy model)? (Choose two.)
An administrator is building a secure, multi-tenant container registry strategy for their vSphere Kubernetes Services deployment running on VMware Cloud Foundation. Each workload domain hosts a Supervisor Cluster, and multiple development teams require private repositories to store and distribute container images for Kubernetes clusters. The organization enforces strict image security posture due to compliance requirements. The operations team deploys Harbor as an add-on service through the Supervisor control plane, and developers push/pull images from Harbor through Kubernetes manifests.
What requirement describes the role and purpose of Harbor?
What component is used to provision VMware vSphere Kubernetes Service (VKS) service mesh workload clusters?
An architect is meeting with a customer to deploy a mission-critical application using the vSphere Kubernetes Service. The architect learns that the ticketing application runs at a steady state 80% of the time but has significant spikes when an event is announced. The application is unable to meet demand even though resources are available.
What will address the issue of peak demand?
What is the function ofContourin a VMware vSphere Kubernetes Service (VKS) cluster?
An administrator is tasked with making an existing vSphere Supervisor highly available by adding two additional vSphere Zones. How should the administrator perform this task?
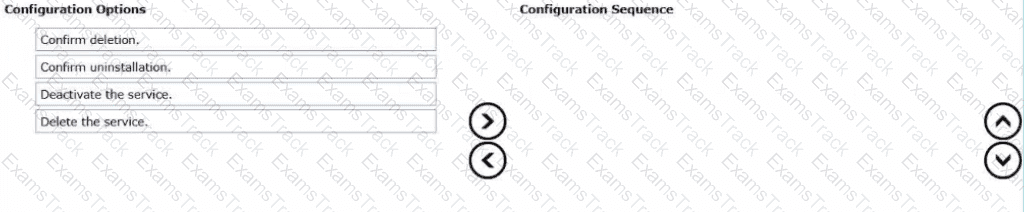
The administrator has completed a proof of concept for using Harbor as a container registry part of the Supervisor services and you are tasked for cleaning up the environment, starting with the unlnstall of the Harbor Supervisor service.
Drag and drop the four tasks into the correct order from Configuration Options on the left and place them into the Configuration Sequence on the right. (Choose four)
An administrator is deploying a vSphere Supervisor with NSX. What will determine the deployment size for the load balancer?
A customer is required to enhance the security for a set of VMware vSphere Kubernetes Service (VKS) clusters that host services interacting with sensitive customer data. The solution must encrypt the transport and communications between services.
The VKS Admin recommends enabling Istio Service Mesh to satisfy the requirement. What type of encryption does Istio Service Mesh provide?
What are three resource limitations defined on a vSphere Namespace? (Choose three.)
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
VMware Free Exams |
|---|

|