Click the Exhibit button.
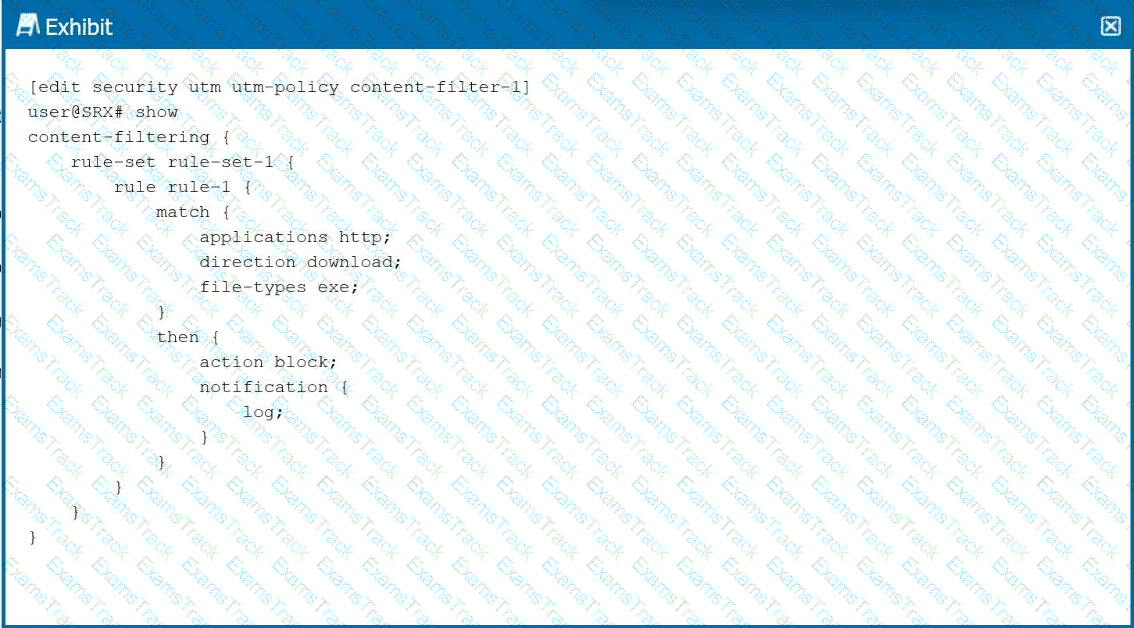
Which two statements are correct about the content filter shown in the exhibit? (Choose two.)
Which two statements are correct about security zones and functional zones? (Choose two.)
When does screening occur in the flow module?
What is the purpose of rate-limiting exception traffic in the Junos OS?
What must also be enabled when using source NAT if the address pool is in the same subnet as the interface?
Click the Exhibit button.
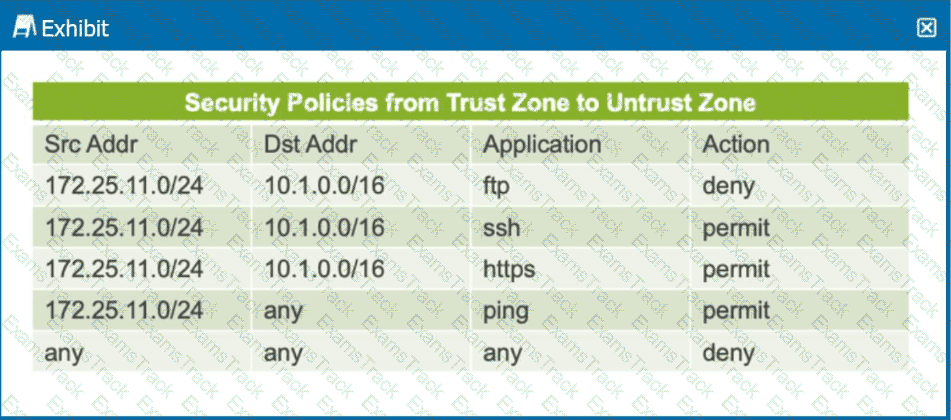
The exhibit shows a table representing security policies from the trust zone to the untrust zone.
In this scenario, which two statements are correct? (Choose two.)
What is the purpose of a feature profile in a UTM configuration?
When a new traffic flow enters an SRX Series device, in which order are these processes performed?
A new packet arrives on an interface on your SRX Series Firewall that is assigned to the trust security zone.
In this scenario, how does the SRX Series Firewall determine the egress security zone?
You want to show the effectiveness of your SRX Series Firewall content filter.
Which operational mode command would you use in this scenario?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Juniper Free Exams |
|---|

|