You work as an Enterprise Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a logging utility class using .NET Framework 3.5. The utility class writes logs to event log services. You are required to ensure that the client applications that use the utility class can create an instance of the utility class only if they have access rights to write to the event log services.
What will you do?
You work as a Software Developer for HiTech Inc. You develop a Web application named
MyWebApp. The application contains several Web pages that display a registration form for a user. You want to perform user input data validation at the server-side, so that you can disable the client-side data input validation. Which of the following actions will you take to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5.
The application rarely experiences errors that cannot be reproduced on a test environment. You are required to ensure that the application meets the following requirements:
l All unanticipated errors are logged.
l Logging is configured with a least amount of alteration to the application code.
What will you do?
Which of the following security methods is used when the code requires a specific set of permissions, which are not known until runtime?
Which of the following provide simplified access to ASP.NET AJAX login, roles, and profile services from Windows Forms and WPF applications?
Which of the following modifiers is not available in C#?
Which of the following syntaxes is used for the EncryptionAlgorithm property of the Message class?
David works as a Software Developer for McRobert Inc. He develops a Web application named App1 using Visual Studio .NET. App1 contains several Web forms that display information about an online shopping process. David wants to provide a Web-based shopping catalog to users. However, he wants to ensure that the information about the shopping catalog is secure and requires no server resources.
What will David do to accomplish the task?
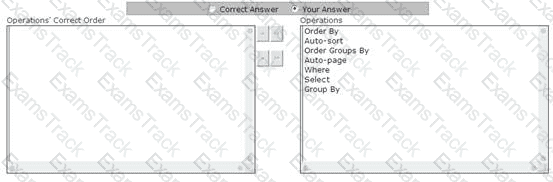
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. The application contains a data-bound control. You use the LinqDataSource control to use LINQ in the ASP.NET application by setting properties in markup text. The LinqDataSource control uses LINQ to SQL to automatically generate the data commands. You are required to perform data operations by using the LinqDataSource control. What is the correct order in which data operations are applied?
Which of the following APIs is used to collect information about any running state and any errors that occur within an ASP.NET application?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|