Which of the following wireless security features provides the best wireless security mechanism?
Which of the following steps are generally followed in computer forensic examinations?
Each correct answer represents a complete solution. Choose three.
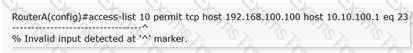
Choose the best explanation for the resulting error when entering the command below.
John works as the Security Manager for PassGuide Inc. He wants to create the Profiler database that stores information about the network activity at Layer 3, Layer 4, and Layer 7. Which of the following will he use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following Wireless LAN standard devices is least affected by interference from domestic appliances such as microwave ovens?
Which of the following is a Cisco IOS management term described in the statement below?
"It is the fourth digit in the configuration register and contains a hexadecimal value. The bootstrap program uses its value to choose which operating system to load into RAM."
You work as a Security Administrator for Tech Perfect Inc. You have implemented and configured a web application security scanner in the company's network. It helps in the automated review of
the web applications with the defined purpose of discovering security vulnerabilities. In order to perform this task, the web application security scanner examines a number of vulnerabilities. What are these vulnerabilities?
Each correct answer represents a complete solution. Choose three.
Which of the following tools is used to analyze the files produced by several popular packetcapture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
Which of the following attacks sends false ICMP packets in an attempt to cripple a system using random fake Internet source addresses?
Which of the following IPv4 to IPv6 transition methods uses encapsulation of IPv6 packets to traverse IPv4 networks?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|