You work as an Information Security Manager for uCertify Inc. You have been assigned the task to list down all procedures included in control A.7.2.2 of the ISO standard. Which of the following procedures are included in control A.7.2.2?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following formulas is used to represent the annualized loss expectancy (ALE)?
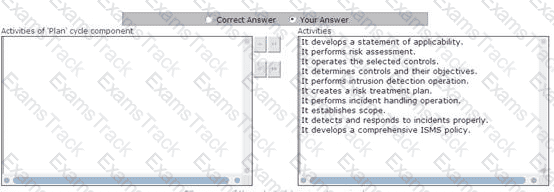
Choose and re-order the activities that are performed by the 'Plan' cycle component of PDCA (plan-docheck- act).
What is the order of the steps in the incident cycle?
Which of the following are the goals of cryptography?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a technique for a threat, which creates changes to the project management plan?
Disaster recovery plan consists of various tiers for identifying the methods of recovering mission-critical computer systems that are necessary to support business continuity. All these tiers provide a simple method to define current service levels and associated risks. Choose and re-order the tiers of disaster recovery plan.
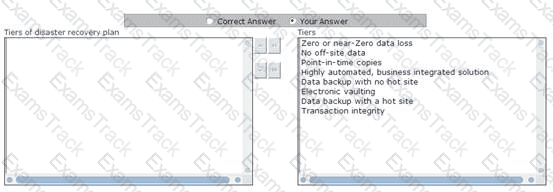
Which of the following provides high availability of data?
Mark works as a Network Security Administrator for uCertify Inc. He has installed IDS for matching incoming packets against known attacks. Which of the following types of intrusion detection techniques is being used?
You are setting up file permissions on a Windows server. Different users have different access needs. What should be your guiding principal in assigning file permissions?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|