John works as a Network Security Professional. He is assigned a project to test the security of
www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.
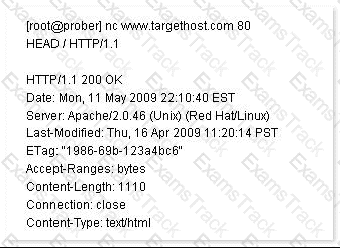
Which of the following attacks is John using?
Which of the following attacks capture the secret value like a hash and reuse it later to gain access to a system without ever decrypting or decoding the hash?
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following wireless network security solutions refers to an authentication process in which a user can connect wireless access points to a centralized server to ensure that all hosts are properly authenticated?
You want to measure the number of heaps used and overflows occurred at a point in time. Which of the following commands will you run to activate the appropriate monitor?
Which of the following attacks allows an attacker to retrieve crucial information from a Web server's database?
Maria works as the Chief Security Officer for PassGuide Inc. She wants to send secret messages to the CEO of the company. To secure these messages, she uses a technique of hiding a secret message within an ordinary message. The technique provides 'security through obscurity'. What technique is Maria using?
Which of the following strategies allows a user to limit access according to unique hardware information supplied by a potential client?
US Garments wants all encrypted data communication between corporate office and remote location.
They want to achieve following results:
l Authentication of users
l Anti-replay
l Anti-spoofing
l IP packet encryption
They implemented IPSec using Authentication Headers (AHs). Which results does this solution provide?
Each correct answer represents a complete solution. Choose all that apply.
Maria works as a professional Ethical Hacker. She has been assigned the project of testing the security of www.gentech.com. She is using dumpster diving to gather information about Gentech Inc.
In which of the following steps of malicious hacking does dumpster diving come under?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|