Adam, a malicious hacker is running a scan. Statistics of the scan is as follows:
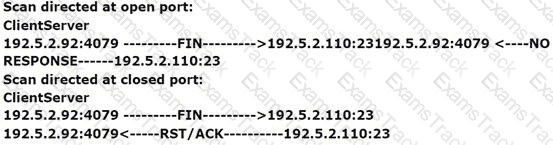
Which of the following types of port scan is Adam running?
The following output is generated by running the show ip route command:
RouterA#show ip route
< - - Output Omitted for brevity - ->
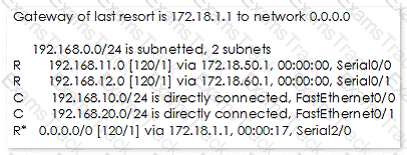
Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
Which of the following tools implements a portable framework in tcpdump for capturing low-level network traffics in UNIX like networks?
Which of the following is the default port for Hypertext Transfer Protocol (HTTP)?
What are the advantages of an application layer firewall?
Each correct answer represents a complete solution. Choose all that apply.
An attacker wants to launch an attack on a wired Ethernet. He wants to accomplish the following tasks:
Sniff data frames on a local area network.
Modify the network traffic.
Stop the network traffic frequently.
Which of the following techniques will the attacker use to accomplish the task?
Which of the following technologies is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single forest multiple domain IPv4 network. All the DNS servers on the network run Windows Server 2008. The users in the network use NetBIOS name to connect network application on the network. Your manager requires you migrate the network to IPv6-enabled network without affecting any client computers. Which of the following actions will you take to accomplish the task?
Which of the following statements are true about routers?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the default port for Simple Network Management Protocol (SNMP)?
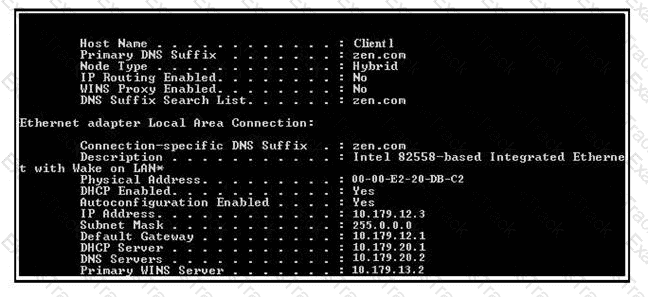
Which of the following utilities produces the output displayed in the image below?
Mark has been assigned a project to configure a wireless network for a company. The network should contain a Windows 2003 server and 30 Windows XP client computers. Mark has a single dedicated Internet connection that has to be shared among all the client computers and the server. The configuration needs to be done in a manner that the server should act as a proxy server for the client computers. Which of the following programs can Mark use to fulfill this requirement?
At which layers of the OSI and TCP/IP models does IP addressing function?
Which of the following is the default port for File Transport Protocol (FTP)?
Which of the following statements about User Datagram Protocol (UDP) is true?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|