John, a novice web user, makes a new e-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a structured approach to transitioning individuals, teams, and organizations from a current state to a desired future state?
Which of the following security design principles supports comprehensive and simple design and implementation of protection mechanisms, so that an unintended access path does not exist or can be readily identified and eliminated?
You work as the Network Security Administrator for uCertify Inc. The organization is using an intranet to distribute information to its employees. A database residing on the network contains employees' information, such as employee name, designation, department, phone extension, date of birth, date of joining, etc. You are concerned about the security because the database has all information about employees, which can help an unauthorized person to recognize an individual. Which Personally Identifiable Information should be removed from the database so that the unauthorized person cannot identify an individual?
Which of the following are the steps of the Do stage of the project?
Each correct answer represents a part of the solution. Choose all that apply.
David has identified a technical risk in his project and has been assigned a contingency for that. Which part of the risk response strategy does planning contingency reserves come under?
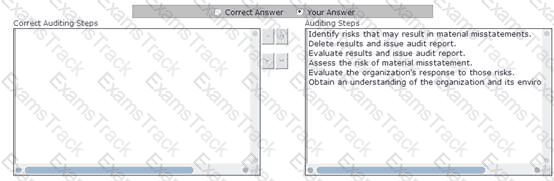
You work as a Network Auditor for Net Perfect Inc. The company has a Windows-based network. You need to audit the network of the company. You need to plan the audit process to minimize the audit risk.
What steps will you take to minimize the possibility of audit risk?
Which of the following is the correct formula of annualized loss expectancy?
Which of the following forms the basis for the assessment of information security management system (ISMS)?
You work as an Information Security Manager for uCertify Inc. You have been assigned the task to create the documentation on control A.7.1.3. Which of the following is the chief concern of control A.7.1.3?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|