Which tool can be used to silently copy files from USB devices?
A botnet can be managed through which of the following?
Which of the following is a symmetric cryptographic standard?
Which of the following is an example of two factor authentication?
Which of the following is an example of an asymmetric encryption implementation?
Which of the following settings enables Nessus to detect when it is sending too many packets and the network pipe is approaching capacity?
While checking the settings on the internet browser, a technician finds that the proxy server settings have been checked and a computer is trying to use itself as a proxy server. What specific octet within the subnet does the technician see?
Which of the following processes evaluates the adherence of an organization to its stated security policy?
From the two screenshots below, which of the following is occurring?
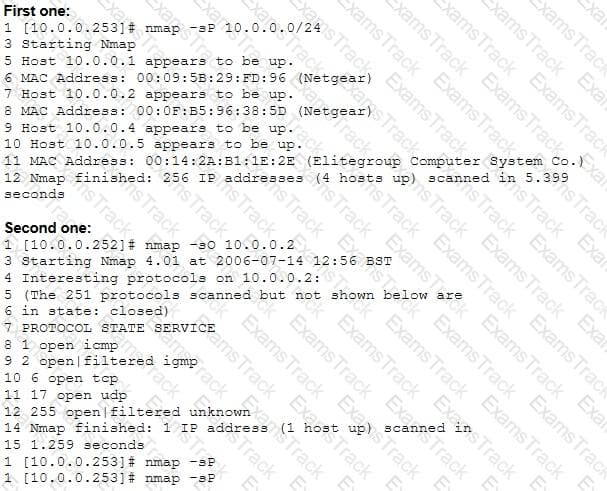
Windows file servers commonly hold sensitive files, databases, passwords and more. Which of the following choices would be a common vulnerability that usually exposes them?
Which of the following problems can be solved by using Wireshark?
Which of the following is a preventive control?
A security analyst in an insurance company is assigned to test a new web application that will be used by clients to help them choose and apply for an insurance plan. The analyst discovers that the application is developed in ASP scripting language and it uses MSSQL as a database backend. The analyst locates the application's search form and introduces the following code in the search input field:
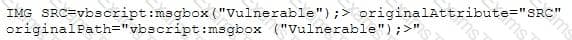
When the analyst submits the form, the browser returns a pop-up window that says "Vulnerable".
Which web applications vulnerability did the analyst discover?
During a wireless penetration test, a tester detects an access point using WPA2 encryption. Which of the following attacks should be used to obtain the key?
In the software security development life cycle process, threat modeling occurs in which phase?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
GAQM Free Exams |
|---|

|