Refer to the Exhibit:
An analyst wants to create an incident and generate a report whenever FortiAnalyzer generates a malicious attachment event based on FortiSandbox analysis. The endpoint hosts are protected by FortiClient EMS integrated with FortiSandbox. All devices are logging to FortiAnalyzer.
Which connector must the analyst use in this playbook?
Refer to the exhibits.
What can you conclude from analyzing the data using the threat hunting module?
Review the incident report:
An attacker identified employee names, roles, and email patterns from public press releases, which were then used to craft tailored emails.
The emails were directed to recipients to review an attached agenda using a link hosted off the corporate domain.
Which two MITRE ATT&CK tactics best fit this report? (Choose two answers)
Based on the Pyramid of Pain model, which two statements accurately describe the value of an indicator and how difficult it is for an adversary to change? (Choose two answers)
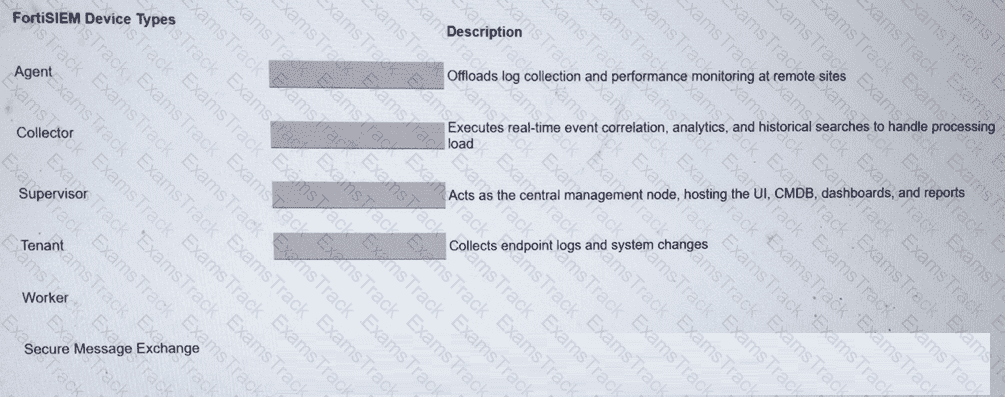
Match the FortiSIEM device type to its description. Select each FortiSIEM device type in the left column, hold and drag it to the blank space next to its corresponding description in the column on the right.
Refer to Exhibit:
You are tasked with reviewing a new FortiAnalyzer deployment in a network with multiple registered logging devices. There is only one FortiAnalyzer in the topology.
Which potential problem do you observe?
What are three capabilities of the built-in FortiSOAR Jinja editor? (Choose three answers)
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|