When configuring anomaly detection machine learning, in which step must you select the fields to analyze?
What can you use to send data to FortiSIEM for user and entity behavior analytics (UEBA)?
Refer to the exhibit.
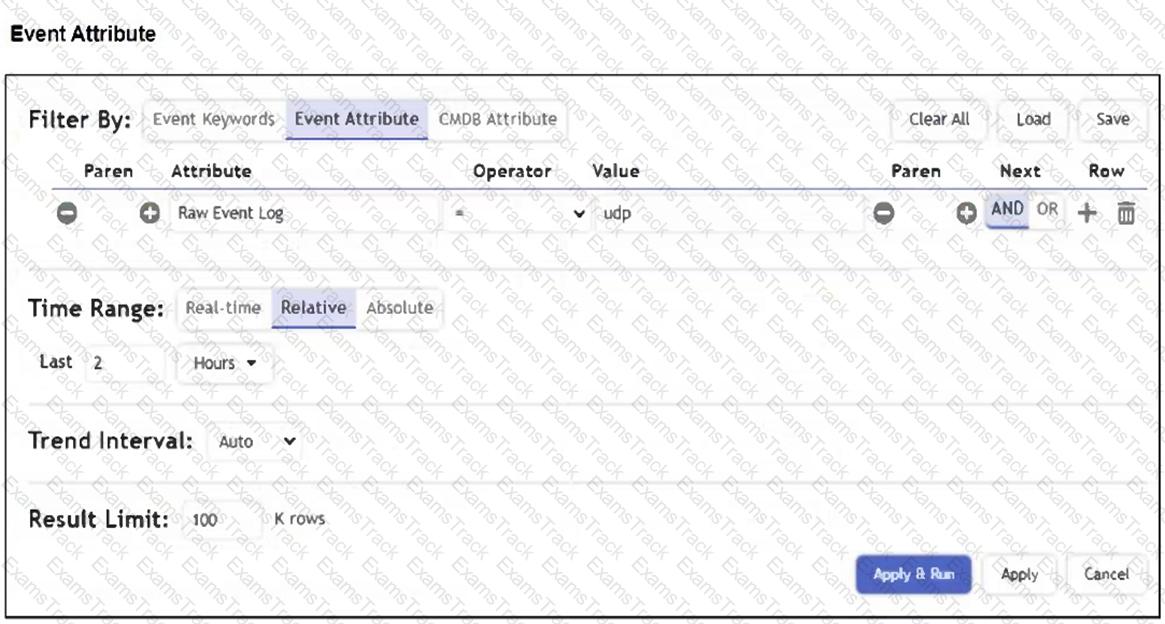
A FortiSIEM device is receiving syslog events from a FortiGate firewall. The FortiSIEM analyst is trying to search the raw event logs for the last two hours that contain the keyword "udp". However, they are getting no results from the search, which they know should be available. Based on the filter shown in the exhibit, why are there no search results?
Refer to the exhibit.
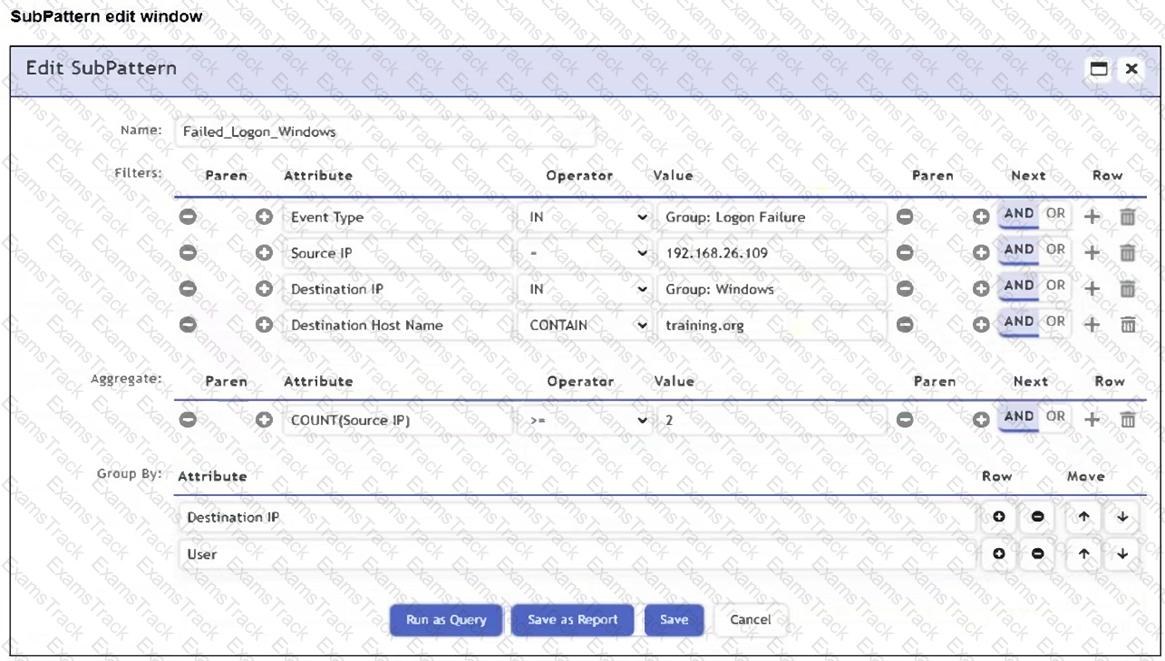
An analyst is troubleshooting the rule shown in the exhibit. It is not generating any incidents, but the filter parameters are generating events on the Analytics tab.
What is wrong with the rule conditions?
Refer to the exhibit.
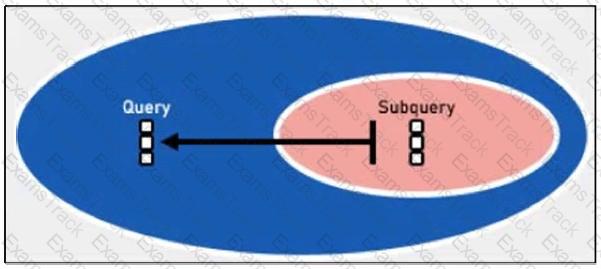
Which two lookup types can you reference as the subquery in a nested analytics query? (Choose two.)
Refer to the exhibit.
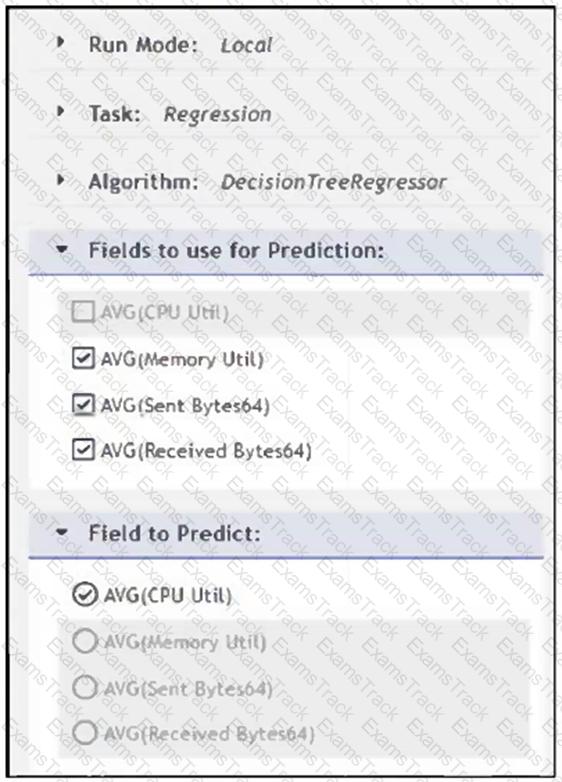
What will happen when a device being analyzed by the machine learning configuration shown in the exhibit has a consistently high memory utilization?
Which items are used to define a subpattern?
Refer to the exhibit.
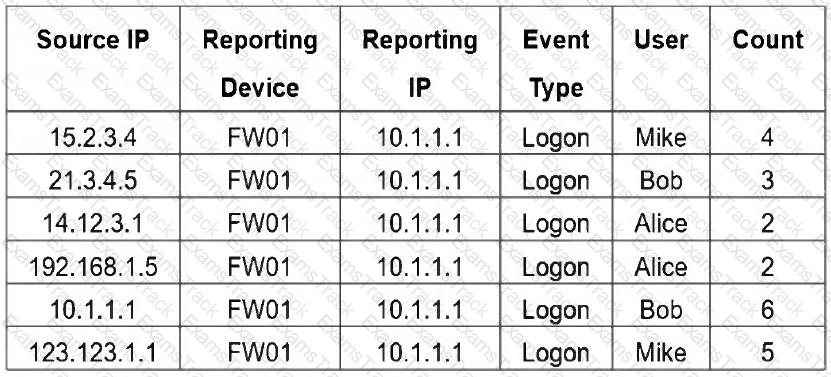
If you group the events by User and Count attributes, how many results will FortiSIEM display?
Refer to the exhibit.
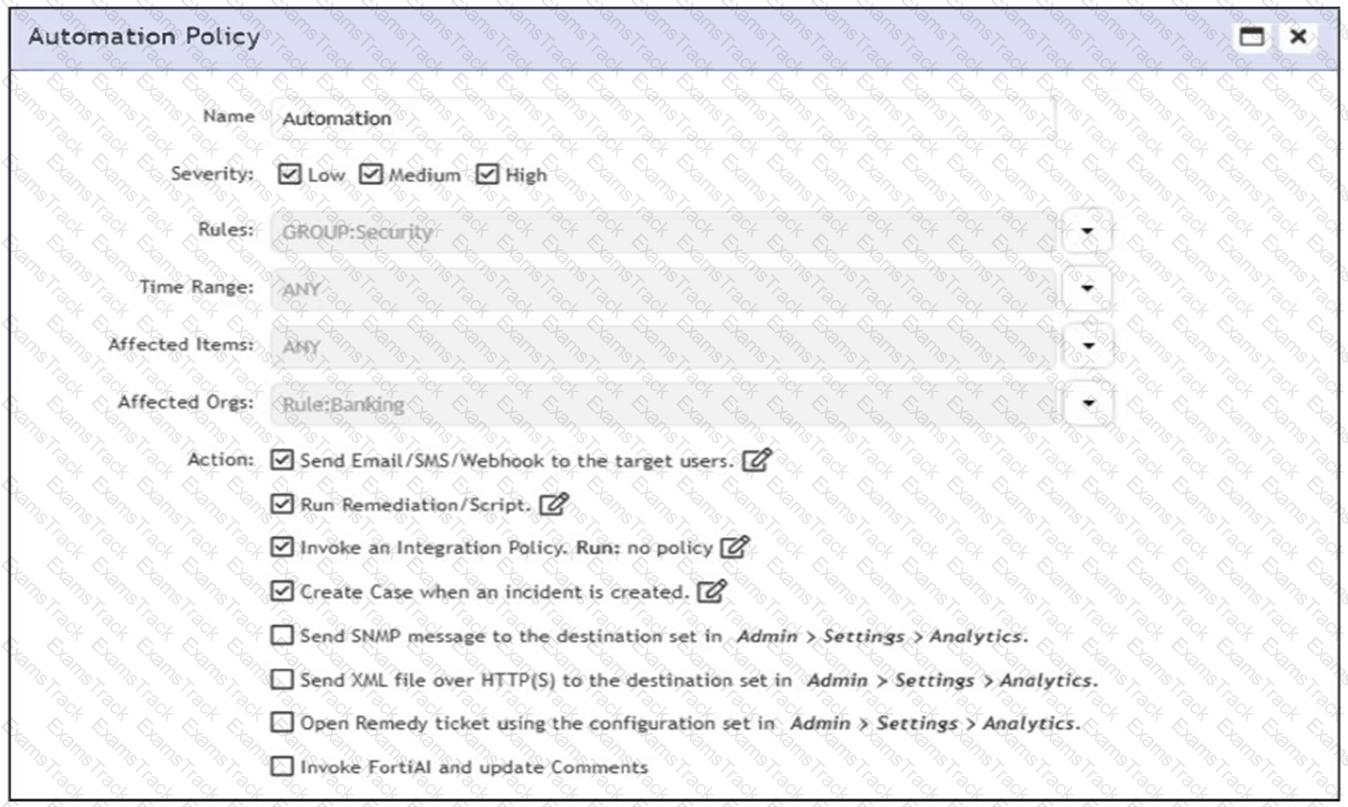
According to the automation policy configuration shown in the exhibit, what happens if an associated rule triggers?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|