Company leadership has discovered an untapped revenue stream within its customer base and wants to meet with IT to share its vision for the future and determine whether to move forward.
Which phase of the software development lifecycle (SDLC) is being described?
What sits between a browser and an internet connection and alters requests and responses in a way the developer did not intend?
The software security team prepared a detailed schedule napping security development lifecycle phases to the type of analysis they will execute.
Which design and development deliverable aid the team prepare?
What is a best practice of secure coding?
Which secure coding best practice says to use well-vetted algorithms to ensure that the application uses random identifiers, that identifiers are appropriately restricted to the application, and that user processes are fully terminated on logout?
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
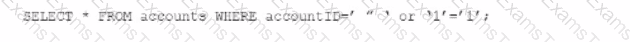
Which technique should be used to detect this vulnerability without running the source codes?
During fuzz testing of the new product, random values were entered into input elements Search requests were sent to the correct API endpoint but many of them failed on execution due to type mismatches.
How should existing security controls be adjusted to prevent this in the future?
What is a countermeasure to the web application security frame (ASF) data validation/parameter validation threat category?
In which step of the PASTA threat modeling methodology will the team capture infrastructure, application, and software dependencies?
The organization has contracted with an outside firm to simulate an attack on the new software product and report findings and remediation recommendations.
Which activity of the Ship SDL phase is being performed?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
WGU Free Exams |
|---|

|