(When access authentication is deployed on a network, which of the following servers typically reside in the pre-authentication domain?)
(The following figure shows a policy control matrix on a virtualized network deployed using iMaster NCE-Campus. Which of the following statements about the policy control matrix are true?Choose all that apply.)

(Which of the following statements about configuring user access authentication is false?)
(Which of the following commands needs to be run in the BGP view to enable a VPN instance to advertise IP routes to the BGP-EVPN address family?)
(An MSP administrator creates a tenant account. Which of the following logs records the operation?)
(Which of the following is used to implement inter-subnet communication on a VXLAN network and allow access from a VXLAN network to an external non-VXLAN network?)
(Based on the VXLAN tunnel creation mode, what are the different types of VXLAN tunnels?)
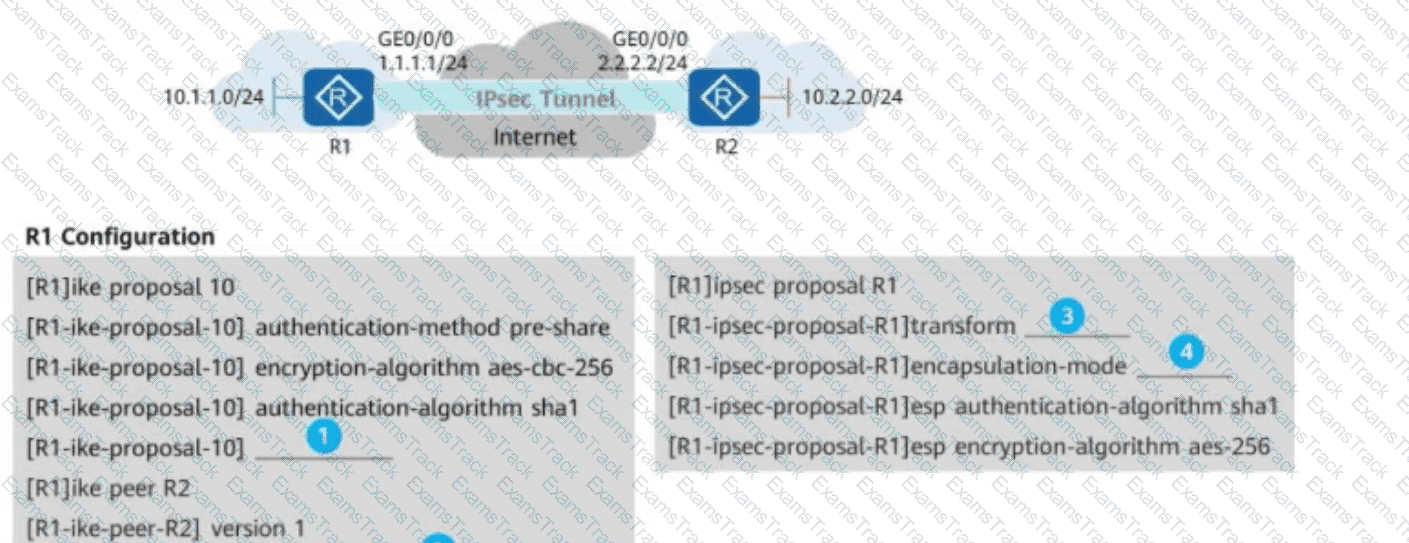
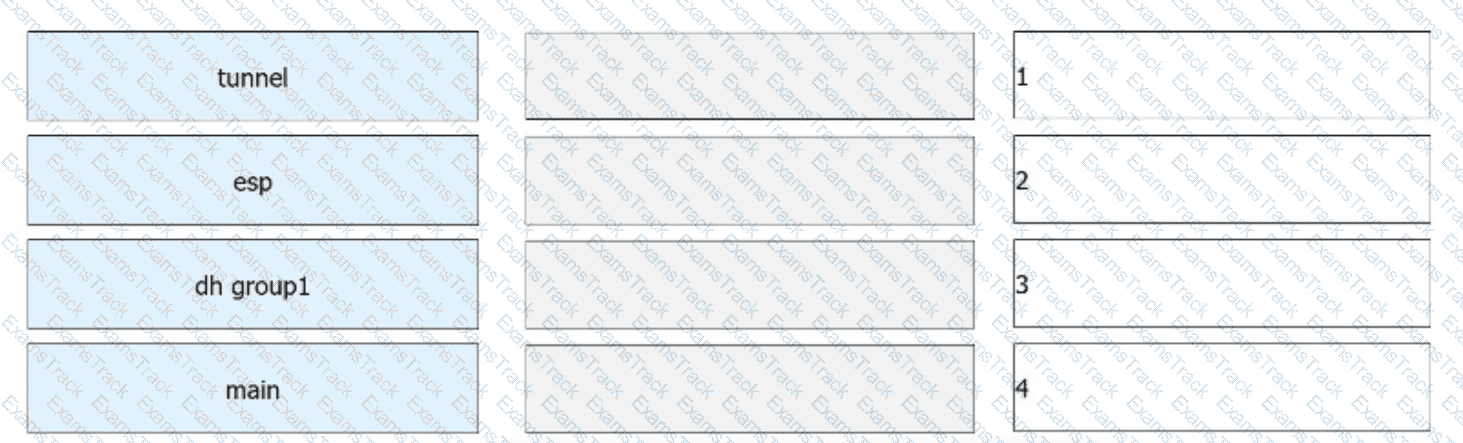
(As shown in the following figure, R1 and R2 establish an IPsec VPN in ISAKMP mode for communication. For IPsec proposals on R1 and R2, ESP is used, the encapsulation mode is set to tunnel mode, SHA1 is configured as the authentication algorithm, and AES-256 is configured as the encryption algorithm. In addition, IKEv1 is configured for IKE peers, the main mode is configured for IKEv1 negotiation phase 1, and the PSK Huawei@123 is configured for PSK authentication between IKE peers. For IKE proposals on R1 and R2, SHA1 is configured as the authentication algorithm, AES-256 is configured as the encryption algorithm, and DH group 1 is configured for IKE negotiation. Based on these configurations on R1 and R2, drag the configuration items on the left to the correct locations on the right.)

(On a small- or medium-sized campus network, multi-carrier links can be deployed at the egress for backup to ensure egress reliability.)
(O&M personnel for a large-scale event center receive feedback about Wi-Fi access failures. iMaster NCE-CampusInsight provides the function for personnel to view packet exchange processes and locate the root cause. It is found that IP addresses in the DHCP address pool are exhausted, preventing IP addresses from being assigned to mobile terminals. Which of the following functions is used by O&M personnel in this scenario?)
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Huawei Free Exams |
|---|

|