Which of the following is a correct sequence of different layers of Open System Interconnection (OSI) model?
Identify the port in the image given below, which can be connected to the hub to extend the number of ports, and up to 127 devices can be connected to it?
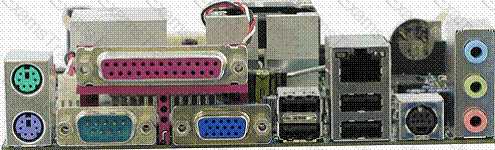
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to allow direct access to the filesystems data structure. Which of the following Unix commands can you use to accomplish the task?
You company suspects an employee of sending unauthorized emails to competitors. These emails are alleged to contain confidential company data. Which of the following is the most important step for you to take in preserving the chain of custody?
Which of the following uses hard disk drive space to provide extra memory for a computer?
Which of the following is used to authenticate asymmetric keys?
Which of the following hardware devices prevents broadcasts from crossing over subnets?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He traceroutes the We-are-secure server and gets the following result:
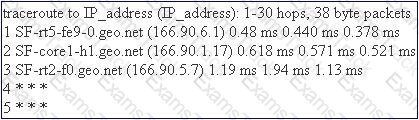
Considering the above traceroute result, which of the following statements can be true?
Each correct answer represents a complete solution. Choose all that apply.
An attacker attempts to gain information about a network by specifically targeting the network resources and applications running on a computer. This method for gaining information is known as ______.
Which of the following types of firewall functions at the Session layer of OSI model?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|