Which of the following is NOT an example of passive footprinting?
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to set the hard disk geometry parameters, cylinders, heads, and sectors. Which of the following Unix commands can you use to accomplish the task?
Mark works as a Network Administrator for Net Perfect Inc. The company has a Linux-based network. Mark installs a Checkpoint Firewall NGX on a SecurePlatform device. He performs a scheduled backup of his system settings and products configuration. Where are these backup files stored?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following directories cannot be placed out of the root filesystem?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as an Incident Handler for Umbrella Inc. He is informed by the senior authorities that the server of the marketing department has been affected by a malicious hacking attack. Supervisors are also claiming that some sensitive data are also stolen. Adam immediately arrived to the server room of the marketing department and identified the event as an incident. He isolated the infected network from the remaining part of the network and started preparing to image the entire system. He captures volatile data, such as running process, ram, and network connections.
Which of the following steps of the incident handling process is being performed by Adam?
You work as a Network Administrator for Peach Tree Inc. The company currently has a FAT-based Windows NT network. All client computers run Windows 98. The management wants all client computers to be able to boot in Windows XP Professional. You want to accomplish the following goals:
The file system should support file compression and file level security.
All the existing data and files can be used by the new file system.
Users should be able to dual-boot their computers.
You take the following steps to accomplish these goals:
Convert the FAT file system to NTFS using the CONVERT utility.
Install Windows XP and choose to upgrade the existing operating system during setup.
Which of the following goals will you be able to accomplish?
Each correct answer represents a complete solution. Choose all that apply.
Nathan works as a professional Ethical Hacker. He wants to see all open TCP/IP and UDP ports of his computer. Nathan uses the netstat command for this purpose but he is still unable to map open ports to the running process with PID, process name, and path. Which of the following commands will Nathan use to accomplish the task?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
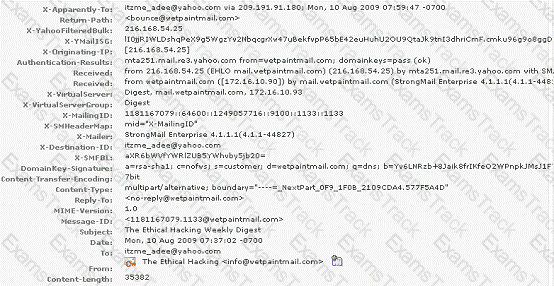
What is the IP address of the sender of this email?
Which of the following modules of OS X kernel (XNU) provides the primary system program interface?
Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned with the project of investigating an iPod, which is suspected to contain some explicit material. Adam wants to connect the compromised iPod to his system, which is running on Windows XP (SP2) operating system. He doubts that connecting the iPod with his computer may change some evidences and settings in the iPod. He wants to set the iPod to read-only mode. This can be done by changing the registry key within the Windows XP (SP2) operating system. Which of the following registry keys will Adam change to accomplish the task?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|