Which command is the Best choice for creating a forensic backup of a Linux system?
Which Unix administration tool is designed to monitor configuration changes to Cisco, Extreme and Foundry infrastructure devices?
How does data classification help protect against data loss?
An outside vulnerability assessment reveals that users have been routinely accessing Gmail from work for over a year, a clear violation of this organization’s security policy. The users report “it just started working one day”. Later, a network administrator admits he meant to unblock Gmail for just his own IP address, but he made a mistake in the firewall rule.
Which security control failed?
Which of the following applies to newer versions of IOS that decrease their attack surface?
The security team wants to detect connections that can compromise credentials by sending them in plaintext across the wire. Which of the following rules should they enable on their IDS sensor?
Which tool keeps a backup of all deleted items, so that they can be restored later if need be?
When running a Nmap UDP scan, what would the following output indicate?
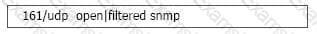
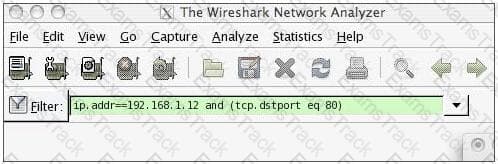
What information would the Wireshark filter in the screenshot list within the display window?
What would a penetration tester expect to access after the following metasploit payload is delivered successfully?
Set PAYLOAD windows / shell / reverse _ tcp
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|