A company estimates a loss of $2,374 per hour in sales if their website goes down. Their webserver hosting site’s documented downtime was 7 hours each quarter over the last two years. Using the information, what can the analyst determine?
Following a Digital Forensics investigation, which of the following should be included in the final forensics report?
If a Cisco router is configured with the “service config” configuration statement, which of the following tools could be used by an attacker to apply a new router configuration?
What is the BEST sequence of steps to remove a bot from a system?
Which type of media should the IR team be handling as they seek to understand the root cause of an incident?
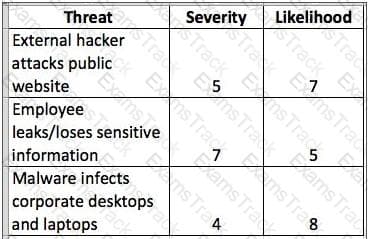
The matrix in the screen shot below would be created during which process?
How does an Nmap connect scan work?
What piece of information would be recorded by the first responder as part of the initial System Description?
What does the following WMIC command accomplish?
process where name=’malicious.exe’ delete
What is the most common read-only SNMP community string usually called?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|