What two permissions must you assign to a user to allow the purge of audit logs for all users? (Choose two answers)
Which two statements about Elasticsearch are true? (Choose two.)
Which three actions can be performed from within the war room? (Choose three)
Which three roles are defined as SAML roles?
(Choose three.)
When deleting a user account on FortiSOAR, you must enter the user ID in which file on FortiSOAR?
Which product is essential to level 3 of the SOC automation model?
Which log file contains license synchronization logs on FortiSOAR?
Several users have informed you that the FortiSOAR GUI Is not reachable. When troubleshooting, which step should you take first?
When configuring the system proxy on FortiSOAR. which two URLs should be accessible from the proxy server? (Choose two.)
Refer to the exhibit.
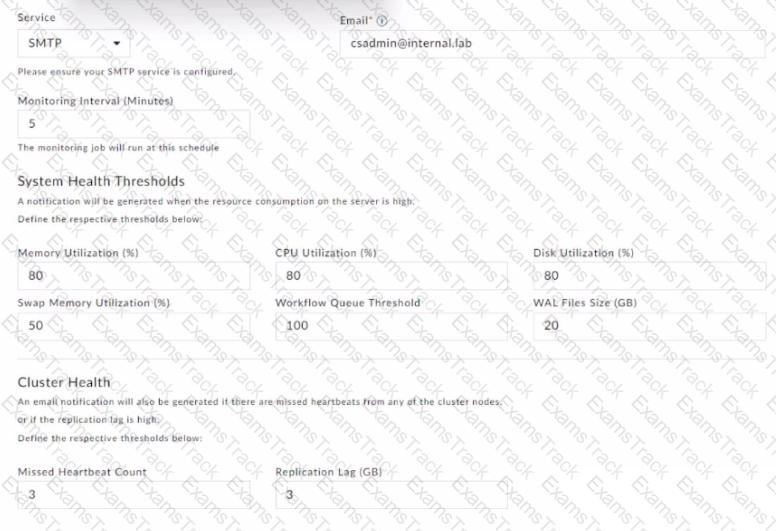
How long after the syops-ha service goes down will the heartbeat missed notification be sent to the administrator?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|