Refer to the exhibit.

The routing tables of FortiGate_A and FortiGate_B are shown. FortiGate_A and FortiGate_B are in the same autonomous system.
The administrator wants to dynamically add only route 172.16.1.248/30 on FortiGate_A.
What must the administrator configure?
Refer to the exhibit.
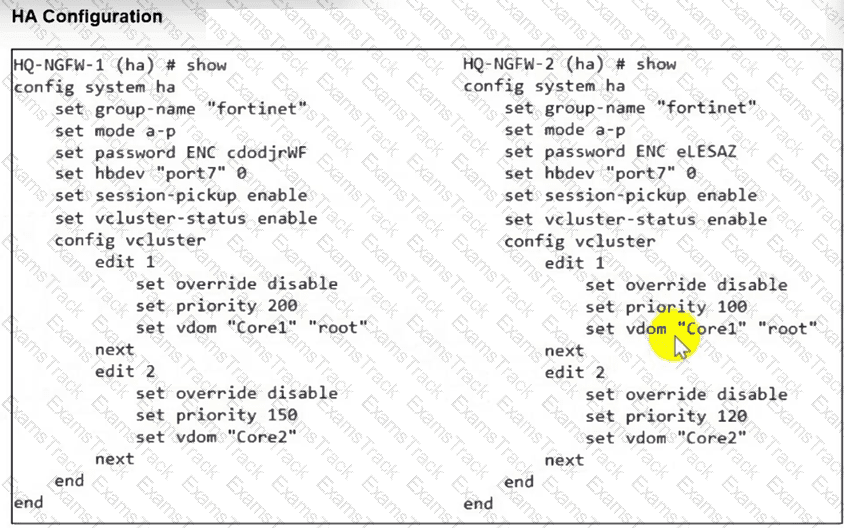
An HA configuration of an active-active (A-A) cluster with the same HA uptime is shown. You want HQ-NGFW-2 to handle the Core2 VDOM traffic. Which modification must you make to achieve this outcome? (Choose one answer)
Refer to the exhibit.
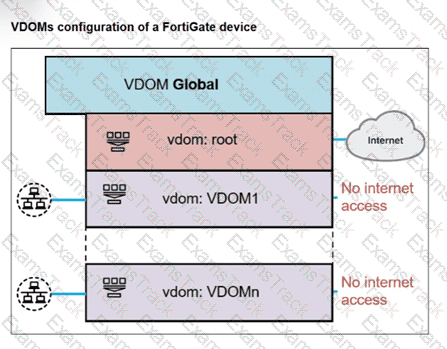
A FortiGate segmented into VDOMs is shown. You must ensure effective and accelerated internet access for all of the VDOMs in this enterprise network. How can you achieve this? (Choose one answer)
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
Refer to the exhibit.
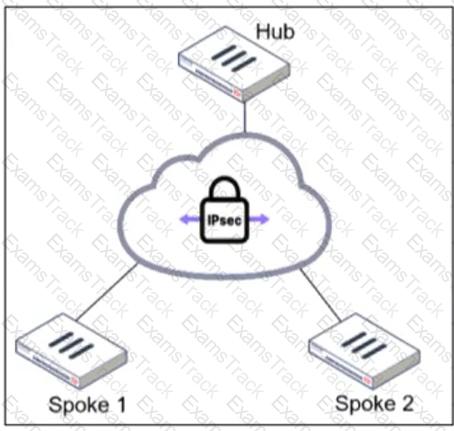
An administrator is deploying a hub and spokes network and using OSPF as dynamic protocol.
Which configuration is mandatory for neighbor adjacency?
Refer to the exhibit, which shows a network diagram showing the addition of site 2 with an overlapping network segment to the existing VPN IPsec connection between the hub and site 1.
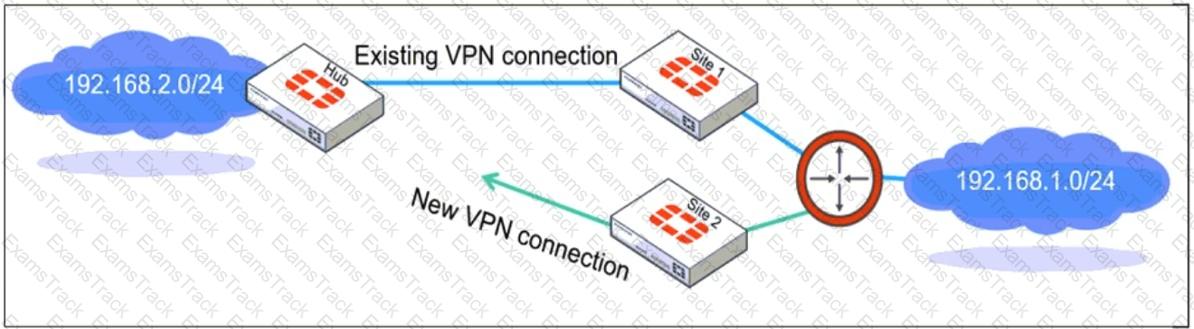
Which IPsec phase 2 configuration must an administrator make on the FortiGate hub to enable equal-cost multi-path (ECMP) routing when multiple remote sites connect with overlapping subnets?
Refer to the exhibit, which shows a hub and spokes deployment.
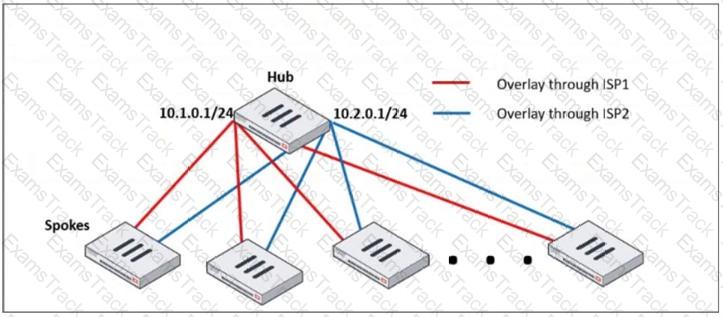
An administrator is deploying several spokes, including the BGP configuration for the spokes to connect to the hub.
Which two commands allow the administrator to minimize the configuration? (Choose two.)
Refer to the exhibit, which shows the VDOM section of a FortiGate device.
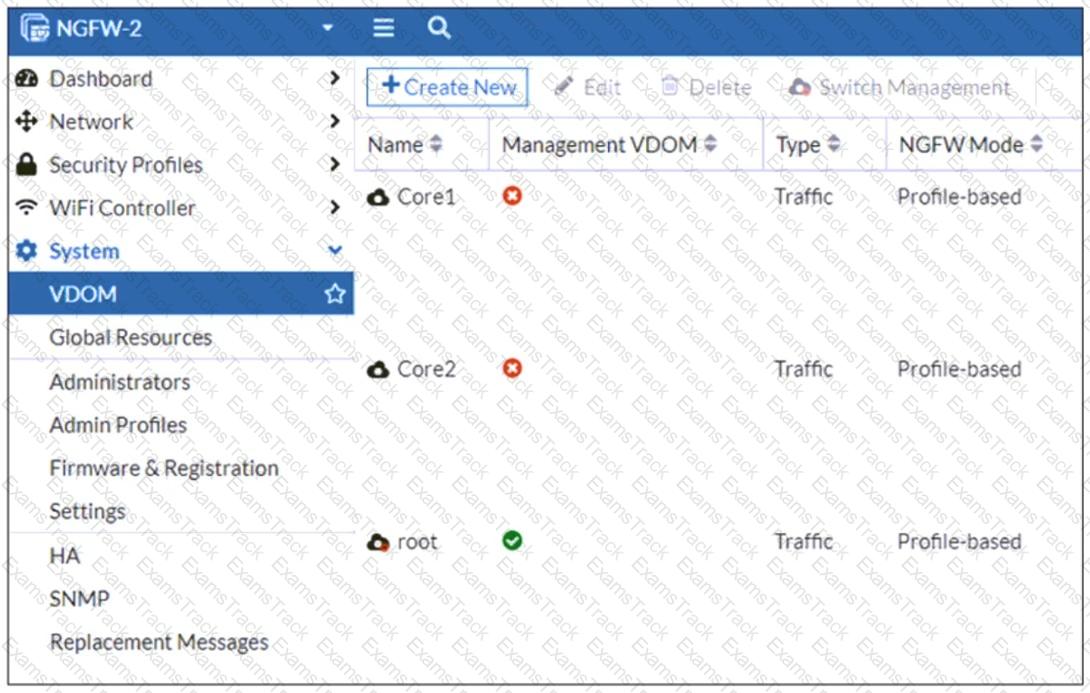
An administrator discovers that webfilter stopped working in Core1 and Core2 after a maintenance window.
Which two reasons could explain why webfilter stopped working? (Choose two.)
Refer to the exhibit.
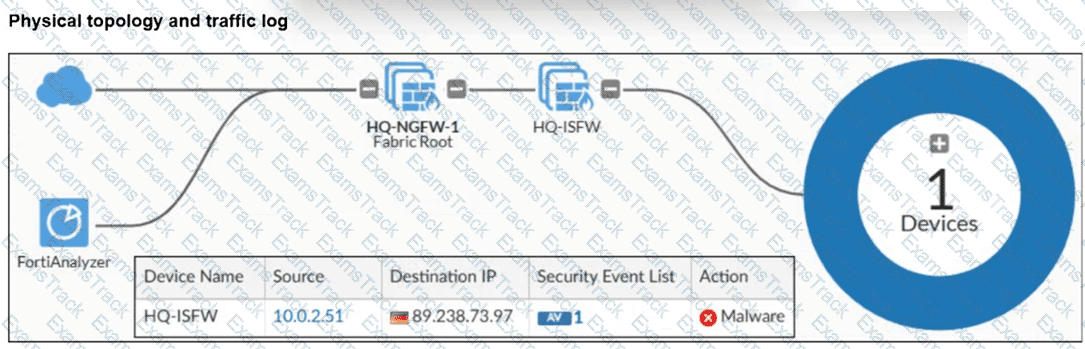
A physical topology along with a traffic log is shown. You are using FortiAnalyzer to monitor traffic from the device with IP address 10.0.2.51, which is located behind the FortiGate internal segmentation firewall (ISFW) device. Unified threat management (UTM) is not enabled in the firewall policy on the HQ-ISFW device, and you are surprised to see a log with the action Malware, as shown in the exhibit. What are two reasons why FortiAnalyzer would display this log? (Choose two answers)
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|