An engineer must design a solution with storage reachability between too physical servers and a storage array. The storage array connectivity is to a SAN switch that Is limited to 46 ports. Which topology meets the requirements without adding more MOS switches?
When planning to deploy a load-balancing service as a managed node, which ACI configuration must be included?
A Cisco engineer is developing a custom application that can run natively in Cisco NX-OS on Nexus 9000 and Nexus 3000 platforms For the NX-SDK application to run the engineer enables the NX-SDK feature on the device Then the NX-SDK is imported into the application via an import nx_sdk_py statement. The engineer creates custom CLI commands and defines custom CLI command syntax within the sdkThread function When CLI commands originate from an NX-SDK application what class is this?
A customer deploys 32 virtualization hosts in a Cisco UCS domain. All hosts run in the same cluster and have Identical hardware specifications. The operating system requires that all firmware is consistent across the hosts (or driver support. The customer must provision additional interfaces later for expandability. Which feature of Cisco UCS Manager meets these requirements?
What are two advantages of using Cisco vPC over traditional access layer designs? (Choose two.)
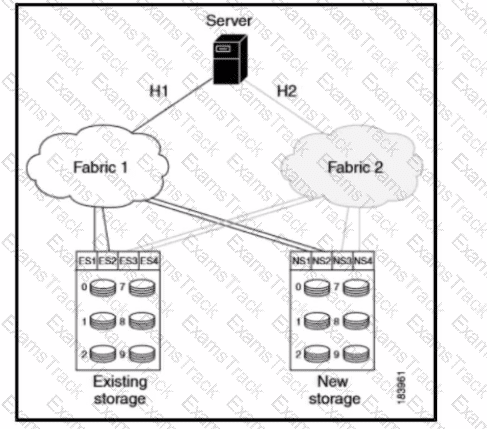
Refer to the exhibit. A Cisco engineer is planning a data migration job in heterogeneous SANs where the existing and new storage devices for the migration are already connected to the MDS switches. All paths from the SSM to the storage-connected switch are going through the Cisco fabric. The setup is with active/active arrays and multiple LUN sets. What is the best approach to copy the LUN sets to the new location?
A network engineer is implementing Cisco UCS manager with Cisco UCS center integration. The company is strict security policies require that the logical profile of virtual network adapters and logical addressing assigned to Cisco UCS servers be managed by the Cisco UCS manager. The users must also be prevented from being able to acknowledge pending activities in the Cisco UCS manager. Which two profile must be used to meet these requirements? (Choose two.)
Which feature provides a sandbox to convert NX-OS CLI commands to REST-based scripts on Cisco Nexus 7700 Series Switches?
An engineer must connect a storage array directly to an existing Cisco UCS Fabric Interconnect. The customer requires a solution that provides IP-based storage that does not need to be connected through an external switch Also, the operations team wants to have the ability to have direct access to the files stored on the storage array from their Linux hosts. Which storage technology meets these requirements?
An engineer must choose the World Wide Port Name for the Cisco UCS Fibre Channel virtual host bus adapter.
Which identifier must be used?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|