The SOC team receives an alert about a user sign-in from an unusual country. After investigating the SIEM logs, the team confirms the user never signed in from that country. The incident is reported to the IT administrator who resets the user's password. Which threat hunting phase was initially used?
During multiple intrusions, analysts observe that attackers consistently perform internal reconnaissance before privilege escalation, avoid noisy exploitation, and limit actions to business hours of the victim’s region. Why is this observation important for attribution?
Refer to the exhibit.
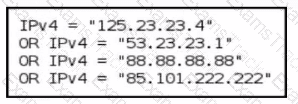
A threat-hunting team makes an EDR query to detect possible C2 outbound communication across all endpoints. Which level of the Pyramid of Pain is being used?
A SOC using Cisco security technologies wants to measure the success of its threat hunting program over time. Which metric BEST reflects increased threat hunting maturity?
After completing a threat hunt that uncovered previously undetected credential abuse, the SOC wants to ensure long-term improvement in detection and response capabilities. Which action BEST represents the final and most critical phase of the threat hunting lifecycle?
A threat hunter wants to detect fileless malware activity usingCisco Secure Endpoint. Which behavior would MOST strongly indicate fileless execution?
While analyzing telemetry from Cisco Secure Endpoint and Secure Network Analytics, analysts observe that an adversary consistently avoids deploying malware and instead abuses built-in administrative tools. Why does this observation matter for attribution?
What is the classification of the pass-the-hash technique according to the MITRE ATT&CK framework?
A structured threat hunt using Cisco Secure Network Analytics confirms abnormal internal SMB traffic consistent with lateral movement. Which action should occur NEXT to improve organizational security posture?
A threat hunter is performing a structured hunt usingCisco Secure Endpoint (AMP)telemetry to identify credential harvesting activity. Which data source is MOST critical during thedata collection and processing phaseof the hunt?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|