Which of the following is used to translate domain names into the numerical (binary) identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide?
John is a black hat hacker. FBI arrested him while performing some email scams. Under which of the following US laws will john be charged?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
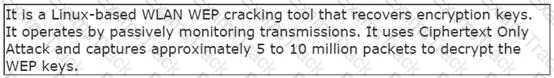
Which of the following tools is John using to crack the wireless encryption keys?
Which of the following would allow you to automatically close connections or restart a server or service when a DoS attack is detected?
You are a project manager of a large construction project. Within the project you are working with several vendors to complete different phases of the construction. Your client has asked that you arrange for some of the materials a vendor is to install next week in the project to be changed. According to the change management plan what subsystem will need to manage this change request?
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for network exploration.
The tool uses raw IP packets to determine the following:
• What ports are open on our network systems
• What hosts are available on the network
• Identify unauthorized wireless access points
• What services (application name and version) those hosts are offering
• What operating systems (and OS versions) they are running
• What type of packet filters/firewalls are in use
Which of the following tools is Victor using?
Which of the following tools is a Windows-based commercial wireless LAN analyzer for IEEE 802.11b and supports all high level protocols such as TCP/IP, NetBEUI, and IPX?
You and your project team have identified the project risks and now are analyzing the probability and impact of the risks. What type of analysis of the risks provides a quick and high-level review of each identified risk event?
Which of the following attacks is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker?
Which of the following attacks does Management Frame Protection help to mitigate?
Each correct answer represents a complete solution. Choose two.
Which of the following is a computer worm that caused a denial of service on some Internet hosts and dramatically slowed down general Internet traffic?
This type of virus infects programs that can execute and load into memory to perform predefined steps for infecting systems. It infects files with the extensions .EXE, .COM, .BIN, and .SYS. As it can replicate or destroy these types of files, the operating system becomes corrupted and needs reinstallation. This type of virus is known as __________.
Rick is the project manager for TTM project. He is in the process of procuring services from vendors. He makes a contract with a vendor in which he precisely specify the services to be procured, and any changes to the procurement specification will increase the costs to the buyer. Which type of contract is this?
Which of the following tasks can be performed by a malicious bot/botnet?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following security protocols can be used to support MS-CHAPv2 for wireless client authentication?
Each correct answer represents a complete solution. Choose two.
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|