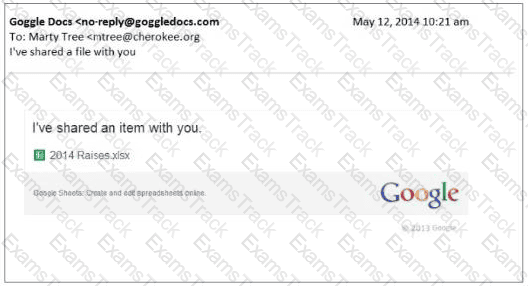
Which of the following actions would best mitigate against phishing attempts such as the example below?
Which of the following best describes the CIS Controls?
A breach was discovered after several customers reported fraudulent charges on their accounts. The attacker had exported customer logins and cracked passwords that were hashed but not salted. Customers were made to reset their passwords.
Shortly after the systems were cleaned and restored to service, it was discovered that a compromised system administrator’s account was being used to give the attacker continued access to the network. Which CIS Control failed in the continued access to the network?
Which of the following CIS Controls is used to manage the security lifecycle by validating that the documented controls are in place?
Which of the following will decrease the likelihood of eavesdropping on a wireless network?
Which of the following archiving methods would maximize log integrity?
When evaluating the Wireless Access Control CIS Control, which of the following systems needs to be tested?
A need has been identified to organize and control access to different classifications of information stored on a fileserver. Which of the following approaches will meet this need?
As part of a scheduled network discovery scan, what function should the automated scanning tool perform?
Acme Corporation performed an investigation of its centralized logging capabilities. It found that the central server is missing several types of logs from three servers in Acme's inventory. Given these findings, what is the most appropriate next step?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|